The PECB ISO/IEC 27005:2022 Risk Manager training course teaches you how to integrate information security risk management guidelines into an organization.
What Is ISO 27005?
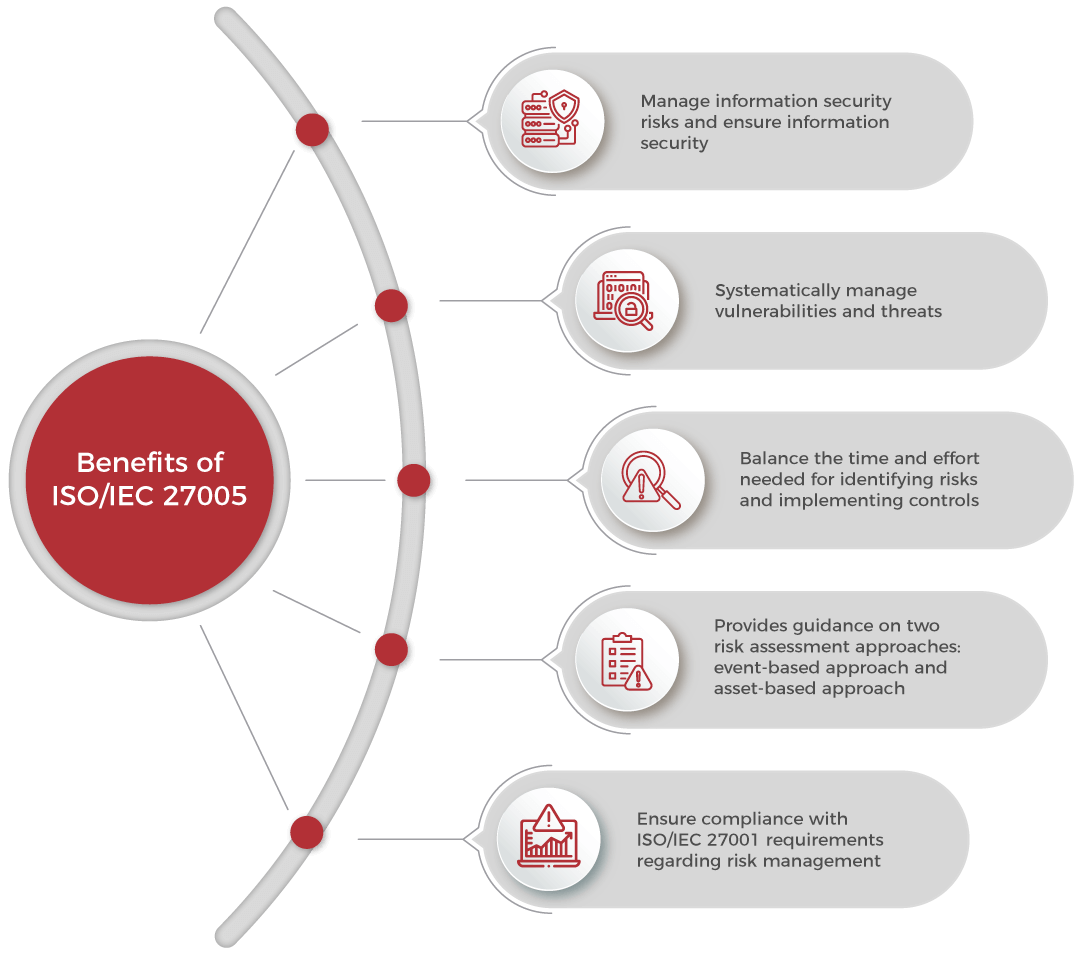
ISO/IEC 27005 provides a risk management framework to manage information security risks. The standard provides guidelines on identifying, analyzing, evaluating, communicating, treating, and monitoring information security risks.
The standard supports the guidelines of ISO 31000 and is particularly helpful for organizations aiming to safeguard their information assets and achieve information security objectives.
The following PECB references are available:
Why Should You Attend?
The PECB ISO/IEC 27005 Risk Manager certification demonstrates that you comprehend the concepts and principles of information security risk management as outlined by ISO/IEC 27005 and also ISO 31000.
This online course will enable you to structure an information security risk management framework and effectively integrate it into the organization. It will help you create a structured approach regarding the identification, analysis, treatment, assessment, and evaluation of risks that are or can be faced by an organization. It also provides an overview of other risk assessment methods, such as OCTAVE, MEHARI, EBIOS, NIST, CRAMM, and Harmonized TRA.
The training course is followed by a certification exam. After successfully passing the exam, you may apply for a “PECB Certified ISO/IEC 27005 Risk Manager” certification which is UKAS accredited and internationally recognized. The certification validates your competence to implement a risk management framework in an organization based on the guidelines of ISO/IEC 27005 and industry best practices
Educational approach
- The training course is based on the theory and the best practices of information security.
- Lecture sessions are illustrated with practical examples and scenarios
- Participants are encouraged to communicate and engage in discussions and exercises
- The quizzes are similar in structure with the certification exam questions
Prerequisites
A fundamental understanding of risk management, processes, and principles.
Examination
The “PECB Certified ISO/IEC 27005 Risk Manager” exam complies with the requirements of the PECB Examination and Certification Program (ECP) and covers the following competency domains:
- Domain 1: Fundamental principles and concepts of information security risk management
- Domain 2: Implementation of an information security risk management program
- Domain 3: Information security risk management framework and processes based on ISO/IEC 27005
- Domain 4: Other information security risk assessment methods
For specific information about exam type, languages available, and other details, please visit the List of PECB Exams and the Examination Rules and Policies.
Certification
After successfully completing the exam, you can apply for the credentials shown on the table below:
| Credential | Exam | Professional experience | Information Security Risk Management experience | Other requirements |
|---|---|---|---|---|
| PECB Ceritified ISO/IEC 27005 Provisional Risk Manager | PECB Certified ISO/IEC 27005 Risk Manager exam or equivalent | None | None | Signing the PECB Code of Ethics |
| PECB Certified ISO/IEC 27005 Risk Manager | PECB Certified ISO/IEC 27005 Risk Manager exam or equivalent | Two years: One year of work experience in ISRM | Information Security Risk Management activities: a total of 200 hours | Signing the PECB Code of Ethics |
You will receive a certificate once you comply with all the requirements related to the selected credential.
To be considered valid risk management experience, the candidate’s activities should follow best practices and include the following:
- Defining a risk management approach
- Determining the risk management objectives and scope
- Conducting a risk assessment
- Developing a risk management program
- Defining risk evaluation and risk acceptance criteria
- Evaluating risk treatment options
- Monitoring and reviewing the risk management program
General Information
- Certification and examination fees are included in the price of the training course
- Training course materials containing over 350 pages of information and practical examples will be distributed to participants
- An attestation of course completion of 21 CPD (Continuing Professional Development) credits will be issued to the participants who have attended the training course
- If you fail the exam, you can retake the exam once for free within 12 months following the initial exam date
Fulfillment
Orders will be fulfilled within 24 hours assuming the student possesses a valid PECB ID number. Register a PECB account to obtain a PECB ID number.



